Categories
Problems that solves
Risk of attacks by hackers
Risk of lost access to data and IT systems
Values
Ensure Security and Business Continuity
Manage Risks
Argus Connected ECU
Prevents, detects, and mitigates attacks targeting connected ECUs, reducing the risk of financial loss, extraction of private data and disruption of vehicle functionality.
About Product
Description
With decades of experience in both cyber security and the automotive industry, Argus offers innovative security methods and proven computer networking know-how with a deep understanding of automotive best practices.
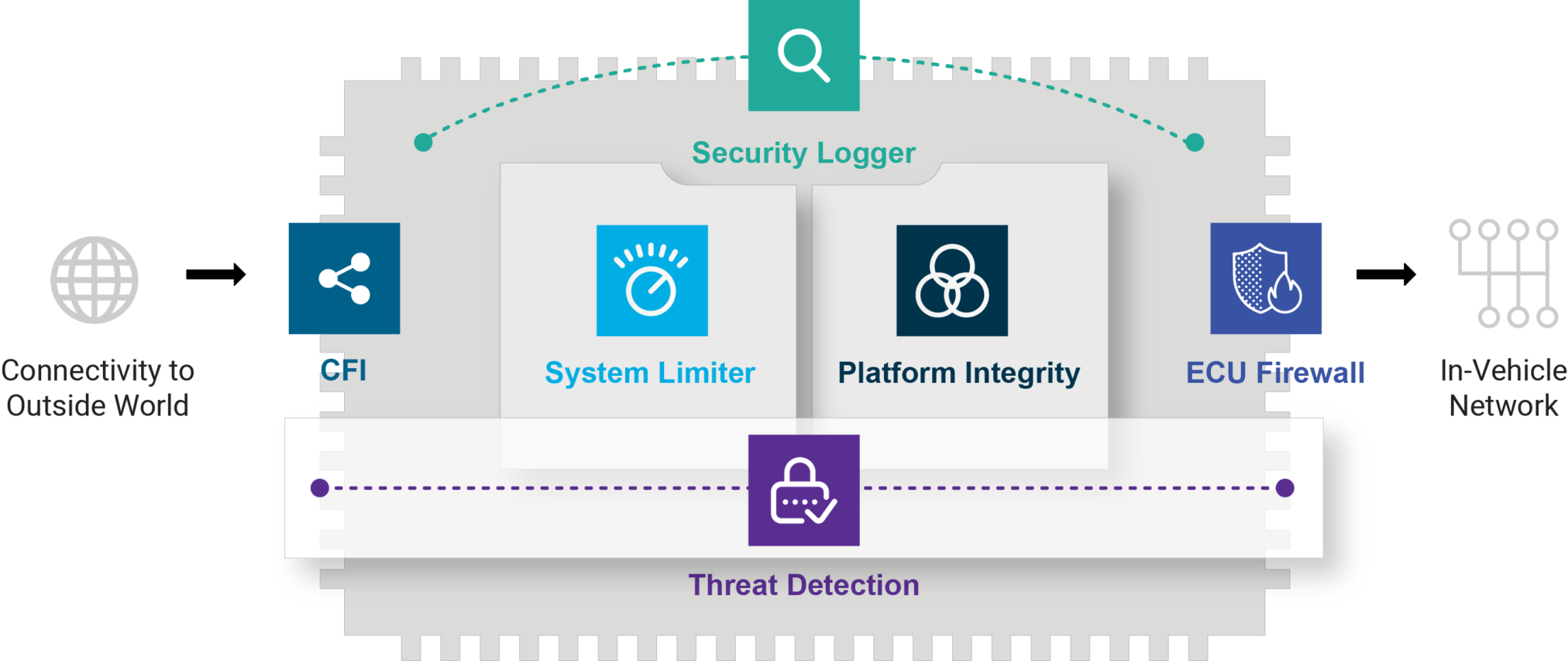
Built for the automotive industry, Argus Connected ECU protection prevents, detects, and mitigates attacks targeting connected ECUs. Six easy to deploy independent modules work individually, or together, to protect the car’s most vulnerable attack surfaces, such as in-vehicle infotainment units (ivis), telematics units (tcus), and adas units.
KEY BENEFITS
AUTONOMOUS. Prevents attacks in real-time without connectivity to the outside world or human intervention MULTI-LAYERED. Provides multiple independent protection layers, to defend against all types of attacks. AUTOMOTIVE-GRADE. Built for the automotive industry and addresses unique automotive security challenges. CONTROL FLOW INTEGRITY (CFI). Prevents exploitation of vulnerabilities, by ensuring that the ECU program does not deviate from its expected execution flow. SYSTEM LIMITER. Prevents unauthorized commands and resource access with an automotive-grade mandatory access control. PLATFORM INTEGRITY. Prevents and blocks unauthorized software from running on the ECU by validating the software at boot and during runtime. SECURITY LOGGER. Collects and securely stores security events from each module, and from other data sources in the ECU, for further analysis by the OEM. THREAT DETECTION. Prevents attacks in real-time, by identifying and responding to suspicious behavior across the ECU that may indicate an unknown attack. ECU FIREWALL. Prevents attacks from spreading to the in-vehicle network by blocking malicious communications using Deep Packet Inspection.KEY FEATURES
- Supports Linux, QNX, and Android operating systems
- Saves time with seamless Integration and easy configuration
- Designed for easy reuse across ECUs
- Consumes minimal system resources
- Supports future module activation
Scheme of work