Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Reduce Costs
Enhance Staff Productivity
CyFIR
CyFIR saves you time, money, and resources with its unparalleled time-to-resolution and network endpoint visibility solutions.
About Product
Description
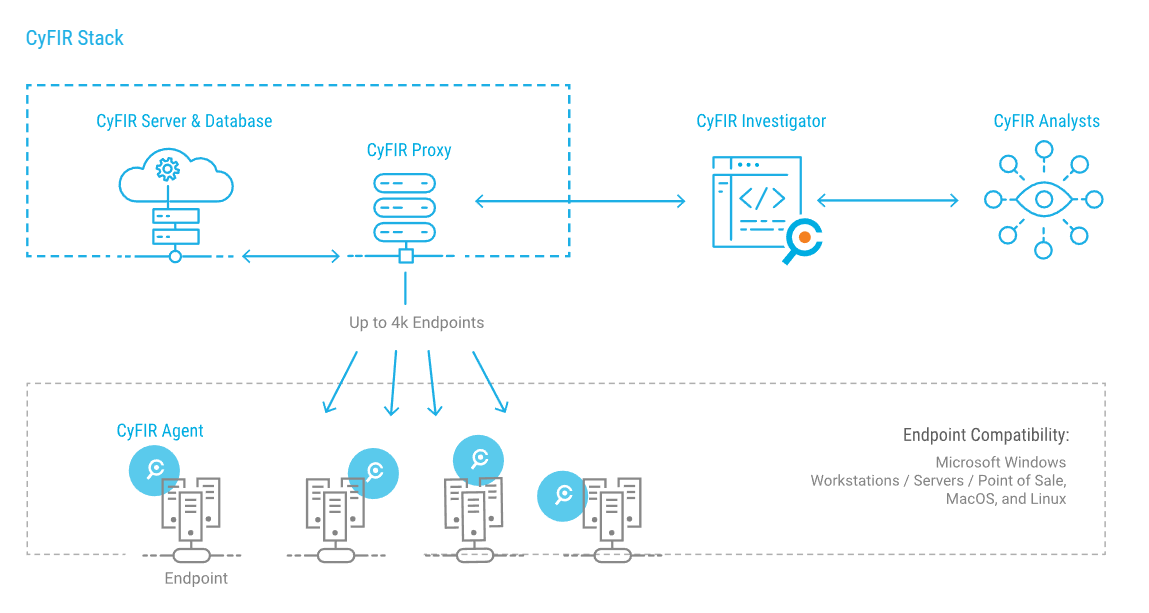
CyFIR is a flexible, remote digital forensics and incident response solution backed by a team of experienced security analysts and practitioners. Whether you are looking to complete your existing security stack, institute an incident response retainer as part of your incident response or mediation strategy, or need immediate help in the aftermath of a breach, CyFIR can provide a solution tailored to your needs.
CyFIR Capabilities:
EDISCOVERY
Fast and accurate document collection without disrupting system performance.
INCIDENT RESPONSE & DIGITAL FORENSICS
Immediate forensic analysis and incident response reduces the cost of a breach by 25 percent or more.
INTERNAL INVESTIGATION
Continuous network security monitoring and access logging of critical network assets.
THREAT ASSESSMENT
Near real-time visibility into network endpoints without impact network operations.
THREAT HUNTING
Proactive, human-centered content profiling and endpoint review.
Benefits:
- Remote. Forensically access computing endpoints across your entire enterprise from a single workstation.
- Live. Search the content of your files for keywords, matching patterns, and more with results appearing as they’re found.
- Speed. Virtually instantaneous forensic-level access to endpoints even in low bandwidth environments.
- Visibility. Near real-time visibility and extraction of RAM, live file systems, deleted data, and unallocated disk space content across your network.
- Accuracy. Comprehensive search and detection capabilities deliver forensically-sound analysis – ensuring good cyber hygiene and improving the fidelity of enterprise-wide queries.
- Integration. Perform forensic tasks without network downtime or user interruption, even when searching Microsoft Exchange mail servers.
- Compatibility. Access forensic artifacts from most versions of Microsoft Windows Workstations / Servers / Point of Sale, macOS, and Linux Systems including data and malware processes obscured by a compromised OS.
Scheme of work