
Categories
Problems that solves
Malware infection via Internet, email, storage devices
Risk of attacks by hackers
Values
Reduce Costs
Ensure Security and Business Continuity
F-Secure Rapid Detection & Response
F-Secure Rapid Detection & Response protects your organization from targeted cyber attacks.
About Product
Description
F-Secure's industry-leading endpoint detection and response (EDR) solution gives you contextual visibility into your security. With our automatic advanced threat identification, your IT team or managed service provider can detect and stop targeted attacks quickly and efficiently.
Key Benefits:
- Gain immediate visibility into your IT environment and security status
- Protect your business and sensitive data by detecting breaches quickly
- Respond fast with expert guidance whenever under attack
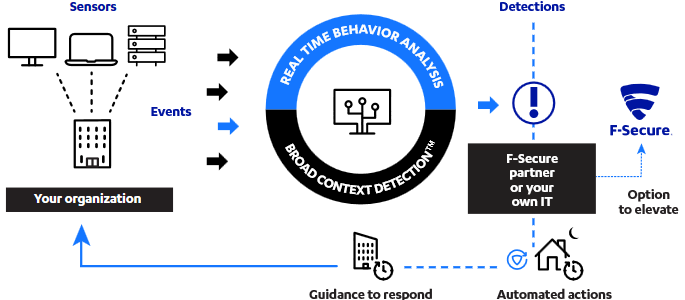
- Lightweight sensors monitor your endpoint users' behavior and stream the events to F-Secure cloud in real-time.
- F-Secure's real-time behavioral analytics and Broad Context Detection distinguish malicious behavior patterns and identify real attacks.
- Visualized broad context and descriptive attack information make confirming a detection easy. F-Secure Partner or your own IT team manages the alerts, and there's an option to elevate tough investigations to F-Secure.
- Following a confirmed detection, our solution provides advice and recommendations to guide you through the necessary steps to contain and remediate the threat.
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
IT Security Department in company
Internet access is available for employees


















