Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Reduce Costs
Enhance Staff Productivity
About Product
Description
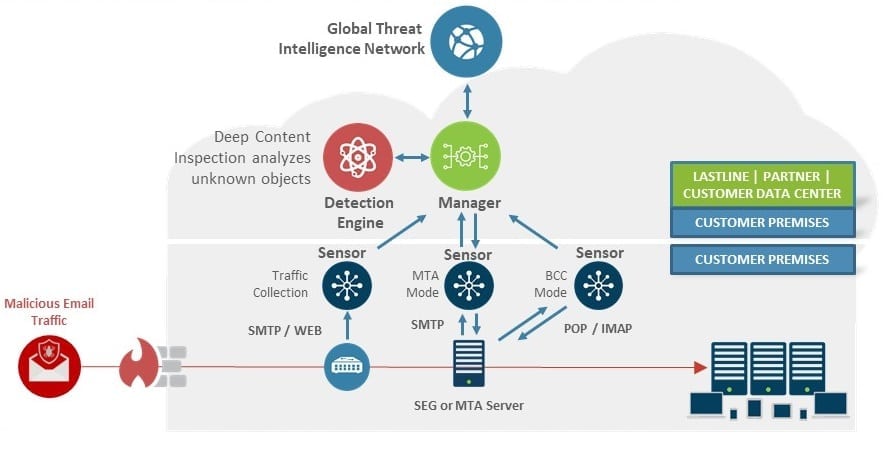
Lastline Defender™ for Cloud Email and Lastline Defender for Customer-Managed Email are complementary layers of defense to enhance your email security controls. You can deploy them anywhere you want to improve your email security against advanced threats engineered to evade detection:
- Lastline Defender for Cloud Email delivers superior Microsoft Office 365 mail and Gmail protection for cloud email systems
- Lastline Defender for Customer-Managed Email protects on-premises or hosted systems
Scheme of work