Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
Shortage of inhouse IT engineers
High costs of IT personnel
Values
Enhance Staff Productivity
Reduce Costs
About Product
Description
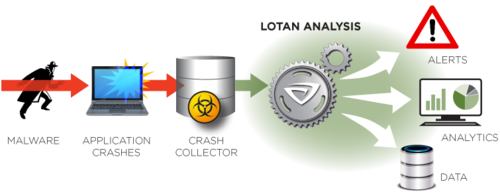
Lotan™ provides your enterprise with the unique capability to detect attacks earlier, and with greater confidence. The fragility of exploits in the face of modern countermeasures and environment heterogeneity often leads to application crashes. Lotan analyzes these crashes to detect the attack and aid the response.
Lotan collects crashes using either a simple registry change on Windows, or a small userland application for Linux.
A RESTful API allows you to share evidence and conclusions with your existing Threat Defense and SIEM solutions. The API provides insight into each step of Lotan's workflow, including detailed information required to understand and respond to the threat rapidly.
Lotan relies on a patent-pending instruction set emulator and classifiers to detect the following exploitation methods and artifacts:
- Heap Spray
- Return-Oriented Programming
- Jump-Oriented Programming
- Corrupted Virtual Pointer
- JIT Spray
- Self-Modifying Code
- Use After Free
- Call Frame Alignment
- Corrupted Function Pointer
- Temporal Anomalies
- Stack Pivots
- Known-Malicious Code
- Automatically detect exploitation of both known and unknown vulnerabilities
- Decrease incident response time
- Increase insight into the health of your network and systems
- Automate event response with confidence
Scheme of work