Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Reduce Costs
Enhance Staff Productivity
Ribbon Communications NetProtect
Redefining the Real-time Communications Security Perimeter
About Product
Description
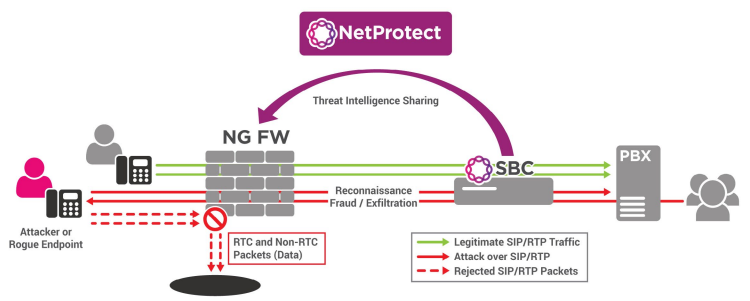
The Threat
Bad actors are constantly looking for ways to cause havoc either for monetary gains, to disrupt internal and external facing customer services, or just do reconnaissance into the entire corporate network. And, the rapid pace of growth for SIP-based real-time communications (RTC) has caught the attention of bad actors.Solution
To address the numerous types of RTC threats, Ribbon Analytics NetProtect application is the answer for your communication network that cannot be secured at any individual device or application layer. NetProtect coordinates RTC protection at the IP, application, and call layers which changes how RTC security is implemented.Ribbon Protect Platform
NetProtect leverages Ribbon’s Protect big data analytics platform to respond to real-time communications security and network quality incidents faster, more intelligently, and more efficiently. The heart of the Protect platform is its UC anomaly detection and policy mitigation capability. The anomaly detection module collects and analyzes data across the entire communications network which is then made available to Ribbon Analytics applications. With customer-defined policy management functionality, detected anomalies generate alerts (e.g. SMS, email) and can be mitigated with actions to the appropriate network elements in real-time. Features & Benefits- Rapidly pinpoints UC security threats and closes the security aperture in your UC network
- Data ingested from Ribbon SBCs and PSX platforms as well as other 3rd party UC network devices
- Disseminate security policies across network “enforcers” such as SBCs and firewalls
- Provides a single repository for an end-to-end view of your network operations
- Virtualized, micro-services architecture for rapid deployment
- No separate hardware or software probes required
- Supports applications for UC security, fraud management and network-wide intelligence
Scheme of work