
Problems that solves
Decentralized IT systems
Inability to forecast execution timelines
Poor timing of management decision making
Risk or Leaks of confidential information
Risk of attacks by hackers
Risk of data loss or damage
Lengthy production timelines
Shortage of information for decision making
Values
Reduce Costs
Enhance Staff Productivity
Ensure Security and Business Continuity
Improve Customer Service
Support Decision Making
Ensure Compliance
Manage Risks
Silverfort
Silverfort protects enterprises from data breaches, cyber attacks and insider threats, by preventing credential compromise and misuse across the entire corporate network and cloud infrastructure.
About Product
Description
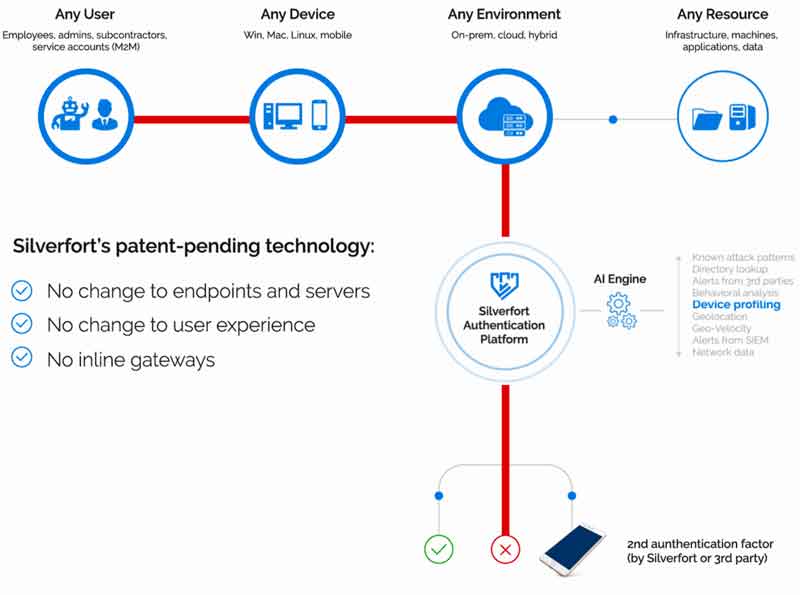
Silverfort enables adaptive multi-factor authentication and identity theft prevention for every sensitive user, device and asset across all environments. Seamlessly deployed, without any software agents or inline gateways, Silverfort allows security teams to protect corporate identities and critical assets, prevent data breaches and address compliance regulations.
Holistic Protection for Any Resource in Any Environment
Protect all authentication and access – by any user or system, via any device, to any application or server, including sensitive resources that could not be protected until today (such as proprietary systems and applications, file servers and IT infrastructure). Protect both employees and application-to-application access to achieve comprehensive protection against data breaches.
Automatically protect resources regardless of their location, even in complex hybrid and multi-cloud environments. Maintain the same advanced protection and visibility layers even when resources are added to the network or moved between different environments (for example during cloud migration), without any integration or change to the resource.
No Change to Clients, Servers and User-Experience
The heart of Silverfort’s technological innovation lies in its ability to enforce strong authentication layers for every user, device and resource, without requiring any configuration or software installation on corporate client devices and servers. Therefore, it only takes a few hours to deploy and start using Silverfort’s authentication platform, even in a large network.
Silverfort’s protection layers are applied seamlessly for every access to the organization’s sensitive resources, without changing user experience. Users can continue to access resources the same way they did before, without any portals or gateways.
Broad Visibility and Actionable Insights
To provide full visibility and protection with minimal integration efforts, the Silverfort platform automatically discovers all users, groups, devices and services in the organization’s network (including in hybrid and multi-cloud environments). It then monitors all authentication and access activity across all systems and environments, to provide comprehensive auditing and actionable insights.
This broad view allows Silverfort to effectively identify authentication vulnerabilities (such as systems that use weak authentication mechanisms and protocols) and detect threats (such as credential theft or insider misuse), which can also be used as a trigger for automatic prevention and step-up authentication policies.
Silverfort also provides a real-time as well as a historic access map of the entire organization, which allows investigating user/device access activity, or identifying access dependencies of a given system (to assure reliable cloud migration, for example).
High Flexibility and Granularity As we all know, security needs are effected by many dynamic factors. New systems and applications are emerging frequently, new regulations are being introduced, business needs are evolving, and even the IT infrastructure itself may change significantly – with cloud migration or an M&A deal. With Silverfort, organizations can dynamically enforce strong authentication wherever it’s required today, and easily adjust it when needed. Silverfort’s ability to protect any authentication scenario with just a few clicks allows it to deliver unparalleled flexibility, which is extremely important in today’s dynamic environments. Silverfort also allows organizations to create custom authentication policies which can fit any scenario. Authentication policies may apply only for specific hours, locations, devices, network segments, protocols, or even based on triggers received from 3rd party security products in real-time. Reduced Total Cost of Ownership Normally, secure authentication products require integration with each protected resource (via software agents, SDKs or configurations). As a result, deployment of new authentication solutions often takes months and includes many challenges. This also means that whenever new users or resources require protection, additional work is needed. Silverfort eliminate these costs, by providing a solution that takes only a few hours to deploy, with no additional efforts for protecting new users and resources – just a few clicks. Silverfort also saves the expensive integration efforts usually required for adding strong authentication into resources that don’t support it (such as proprietary systems).
High Flexibility and Granularity As we all know, security needs are effected by many dynamic factors. New systems and applications are emerging frequently, new regulations are being introduced, business needs are evolving, and even the IT infrastructure itself may change significantly – with cloud migration or an M&A deal. With Silverfort, organizations can dynamically enforce strong authentication wherever it’s required today, and easily adjust it when needed. Silverfort’s ability to protect any authentication scenario with just a few clicks allows it to deliver unparalleled flexibility, which is extremely important in today’s dynamic environments. Silverfort also allows organizations to create custom authentication policies which can fit any scenario. Authentication policies may apply only for specific hours, locations, devices, network segments, protocols, or even based on triggers received from 3rd party security products in real-time. Reduced Total Cost of Ownership Normally, secure authentication products require integration with each protected resource (via software agents, SDKs or configurations). As a result, deployment of new authentication solutions often takes months and includes many challenges. This also means that whenever new users or resources require protection, additional work is needed. Silverfort eliminate these costs, by providing a solution that takes only a few hours to deploy, with no additional efforts for protecting new users and resources – just a few clicks. Silverfort also saves the expensive integration efforts usually required for adding strong authentication into resources that don’t support it (such as proprietary systems).
Scheme of work
Competitive products
User features
Organizational Features
GDPR Compliance
Сonfidential data
Internet access is available for employees
IT Security Department in company


















