
Categories
Problems that solves
Risk or Leaks of confidential information
Risk of data loss or damage
Risk of attacks by hackers
Decentralization of management
No IT security guidelines
Shortage of inhouse IT resources
High costs of IT personnel
Values
Ensure Security and Business Continuity
Manage Risks
Barracuda PhishLine
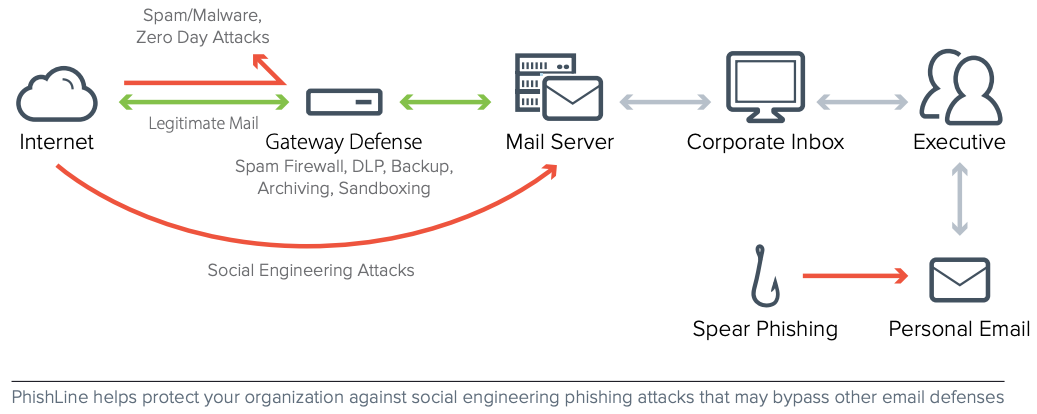
Barracuda PhishLine - Fight phishing with continuous simulation and training Train employees to understand the latest attack techniques, recognize subtle clues, and help stop email fraud, data loss
Description
Fight phishing and other potentially devastating attacks that can slip through security gateways. These evolving and sophisticated attack techniques, designed to fool employees, put your business at risk for data loss, financial fraud, and embarrassing exposure. Transform employees into a layer of defense with Barracuda PhishLine.
With PhishLine, you guard against every facet of social-engineering threats with continuous simulation and training for employees. Expose them to the latest attack techniques, and teach them to recognize the subtle clues and help stop email fraud, data loss, and brand damage. Embed learning into your everyday business processes with customized simulations that test and reinforce good behavior.
Only PhishLine helps you guard against a range of threats with patented, highly-variable attack simulations for multiple vectors, including phishing, smishing, vishing, and found physical media.
Barracuda PhishLine trains users to understand and respond correctly to the latest phishing techniques, recognize subtle phishing clues, and prevent email fraud, data loss, and brand damage. It transforms employees into a powerful line of defense against damaging phishing attacks.
This versatile, scalable, cloud-hosted SaaS solution includes hundreds of email and landing-pages templates, updated based on threat trends. Levelized training and gamification make it more effective by engaging employees.
Phishing Training
Barracuda PhishLine uses advanced, automated education technology that includes simulation-based training, continuous testing, powerful reporting for administrators, and active incident response awareness.
Phishing Simulation
Simulated phishing attacks are constantly updated to reflect the most recent and most common threats. Simulations are not limited to email, but also include voice, SMS, and portable-media (USB stick) attacks. Templates let you customize simulations.
Phishing Reporting
Barracuda Phishline provides advanced analytics and reporting tools that enable you to identify how effective your training is and how users react to actual phishing attacks that may slip through other defenses.
Patented Simulations
PhishLine's patented attack simulations train your employees to spot email threats that can compromise data and result in financial and reputational loss. A/B tests prevent users from receiving duplicate simulations.
Total Email Protection Portfolio
PhishLine is part of Barracuda’s Total Email Protection portfolio, delivering truly comprehensive email security.
Curated Content
PhishLine Content Center Marketplace™ provides dozens of simulation templates, landing pages, risk-assessment surveys, and other training content. New, customizable content is added daily, to reflect current threat trends.
Gamification
PhishLine boosts user engagement with gamification. Videos, infographics, newsletters, and other materials supplement core training.
Levelized Programs
As employees progress through their training program, the content constantly changes, challenging them to continuously improve their phishing detection and reporting skills.
PhishLine Concierge Service (Optional)
PhishLine Concierge is an optional service that offloads the complex tasks of defining, configuring, executing, and analyzing your simulation campaigns to a dedicated consultant, to minimize your resource overhead.
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
GDPR Compliance
ISO 27001 Compliance
IT Security Department in company
Web-based customer portal
Company branches in different countries





