Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Reduce Costs
Enhance Staff Productivity
About Product
Description
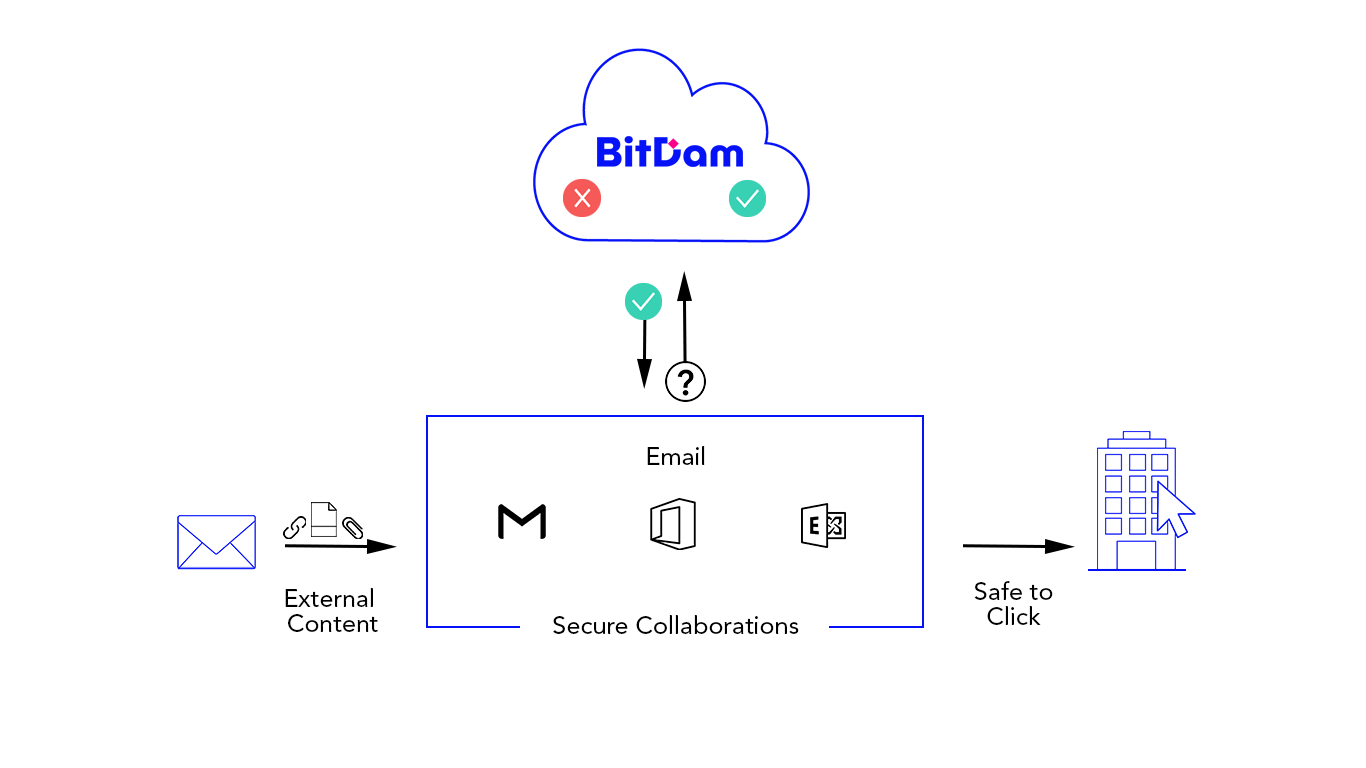
Email, shared URL’s, file attachments, cloud drives and new digital communications are transforming the way we work. They are also the most accessible entry point for advanced content-borne cyber attacks.
Deep Application Learning
Continuous and aggregative CPU-level learning of application paths. BitDam live knowledge base of all legitimate executions for common business applications. Real-time analysis, code benchmarking and immediate alien code detection for advanced threats, regardless of the specific attack technique.
Alien Code Detection Forever Protected Applications
100% attack code visibility for known and unknown threats, covering all attachments & links. Prevention of sophisticated exploits and evasion methods, pre-code execution. No need for security updates or patches.
BitDam Email Security & Malware Protection Features
- Close to zero latency – With minimal email latency of just a few seconds, end-users will not notice any change. With BitDam, they’re safe to click everything that lands in their inbox.
- 2-click integration – Pre-built APIs enables a (literally) 2-click self-service deployment through the BitDam portal, which applies for all mailboxes in the organization.
- Fast and easy deployment – No MX record change is needed, no hassle to your IT team.
- Intuitive dashboard – Your SOC team can view email subject and recipients through the BitDam dashboard, making tracking and investigating attacks simple.
- Email body and clean files are never saved – BitDam scans the entire email including links and attachments, but doesn’t save it unless malicious.
- Quarantine malicious emails – Malicious emails are automatically quarantined, allowing the SOC team to investigate, delete or release them as needed.
- Visibility to other security checks – As a SOC team user you can see what basic security checks each email went through. This includes anti-spam, spf, and dmarc checks.
- Cloud Storage
- Instant Messaging
Scheme of work