
Categories
Problems that solves
No monitoring of corporate IT processes
No automated business processes
Unstructured data
Low employee productivity
Risk of lost access to data and IT systems
Decentralization of management
Insufficient risk management
No control over implementation
Values
Reduce Costs
Enhance Staff Productivity
Ensure Security and Business Continuity
Centralize management
Manage Risks
Cyberbit Range
Cyberbit Range is the most widely deployed Cyber Security Training and simulation platform
About Product
Product presentation
Description
Security Teams are not Ready
Eventually, your organization will be attacked. When this happens, your SOC team’s skillsets, including playbook knowledge, detection and investigation skills, teamwork and communication skills, and security tool operation, will be put to the test. However, conventional training courses do not prepare incident response teams for the intense experience of a cyberattack. SOC teams are unprepared and overwhelmed.
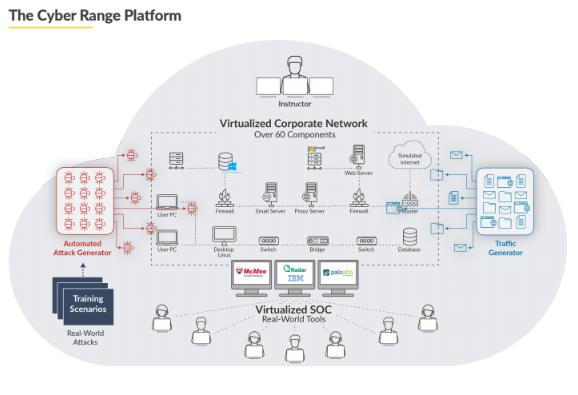
Cyberbit Range: Simulating the Cyberattack Experience Cyberbit Range was created to address this critical gap. It introduces a new training approach by providing a hyper-realistic, virtual SOC environment, where your team can train in responding to real-world, simulated cyberattacks and dramatically improve their skills.
Instant, Cloud-Based Training Your SOC team’s time is precious. Their training needs to be accessible, so they can train before or after their shift without leaving the office. By training with Cyberbit Cloud Range, your team can log in anytime, anywhere, and start a simulated training session within minutes, either individually, or as a team.
Cyber Range Simulated Training
Cyberbit Range: Simulating the Cyberattack Experience Cyberbit Range was created to address this critical gap. It introduces a new training approach by providing a hyper-realistic, virtual SOC environment, where your team can train in responding to real-world, simulated cyberattacks and dramatically improve their skills.
Instant, Cloud-Based Training Your SOC team’s time is precious. Their training needs to be accessible, so they can train before or after their shift without leaving the office. By training with Cyberbit Cloud Range, your team can log in anytime, anywhere, and start a simulated training session within minutes, either individually, or as a team.
Cyber Range Simulated Training
- Train Groups or Individuals
- Train Blue or Red Teams
- Train any Role From Tier-1 Analysts to Executives
- Guided or Independent Training with Automated Assessment
- Entry-Level to Complex Scenarios
- Cloud Based Access - Anytime, Anywhere
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief Technical Officer
Chief IT Security Officer
Other CxO
Organizational Features
Internet access is available for employees
Backup data center
GDPR Compliance
Own Data Center





