Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Enhance Staff Productivity
Reduce Costs
About Product
Description
NC Protect’s helps enforce compliance and data security policies for privacy and confidentiality, intellectual property and trade secret protection, data loss prevention, enterprise social communications, PII and PCI compliance, HIPAA requirements, and other governance factors. It ensures data compliance and security by continuously monitoring and auditing data and documents against regulatory and corporate policies to protect against data breaches, unauthorized access and misuse.
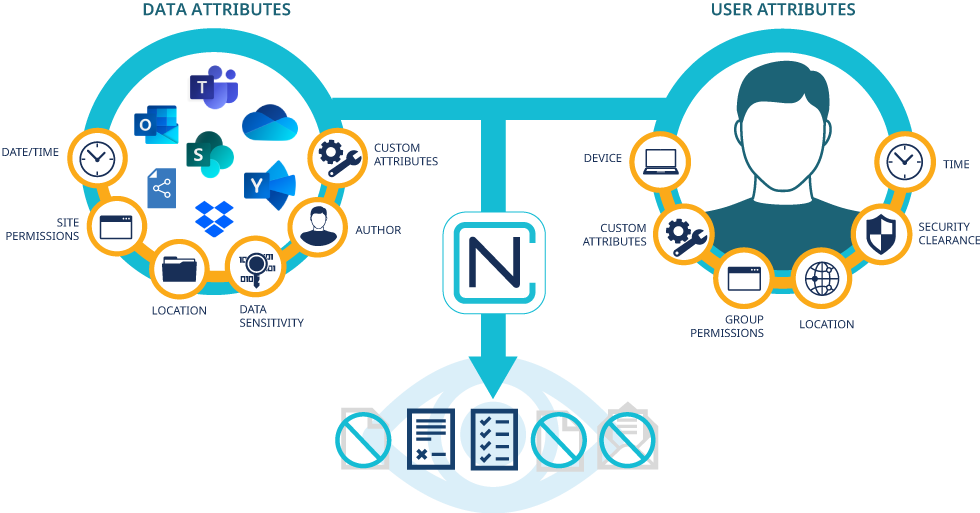
Dynamically control access and data protection using file content & user context
Discover and Classify Data Locate sensitive data (PII, PHI, IP, etc.) using a single set of rules for one or multiple environments and automatically classify it based its sensitivity and your governance policies. Define who can classify or reclassify data, unlike standard metadata that can be modified by anyone with file access. Control Access and Sharing Utilize granular security to automatically restrict access to, restrict sharing of and encrypt content based on the presence of sensitive data including PII, PHI and other confidentiality factors. Track Access Track access to sensitive data, ensuring transparency and accountability. Dynamically add a watermark to Word, PowerPoint, Excel and PDF documents for security and auditing purposes. Multi-environment Protection Centrally control access and user actions using a single solution to protect content on-premises, in the cloud and in hybrid environments including Microsoft Office 365, SharePoint, Teams, Yammer, Dropbox and files shares.Scheme of work