Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Reduce Costs
Enhance Staff Productivity
About Product
Description
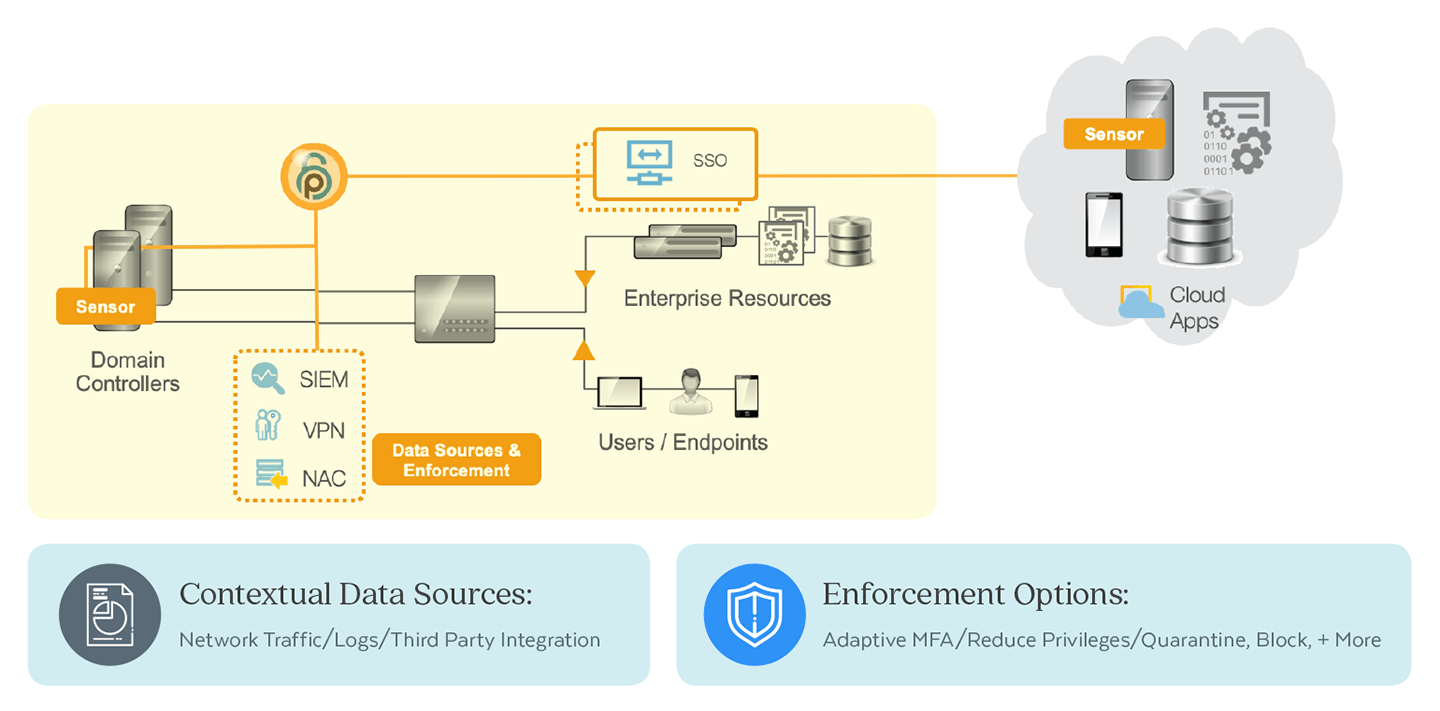
Preempt empowers organizations to easily reduce user risk on their attack surface and preempt threats in real time with Conditional Access. Our patented technology continuously analyzes, adapts and responds to threats based on identity, behavior and risk to auto-resolve insider threats and targeted attacks.
Identity and Risk Insights
Preempt provides a continuous health and risk assessment revealing password problems, privileged access, stale accounts, stealthy admins, Active Directory (AD) configuration issues and more. Actionable insights allow your security team to easily reduce risk and your attack surface making it easier to pass your next audit.
Understand Identity Everywhere
Continuously discover all users
- Privilege Users
- Stealthy Admins
- Stale Accounts
- Employees
- Service Accounts
- Weak Passwords
- NTLM Hashes
- Inactive Accounts
- Vulnerable OS
- Users or Admins with SPN’s
- Reset Password
- Demote User
- Isolate User
- Disable User or Accounts
- And more
Scheme of work