Problems that solves
Unauthorized access to corporate IT systems and data
No centralized control over IT systems
Non-existent or decentralized IT incidents' management
No control over the state of communication channels
IT infrastructure downtimes
Values
Reduce Costs
Ensure Security and Business Continuity
Centralize management
Enhance Competitive Ability
Rhebo Industrial Protector
Industrial Protector is the passive, non-intrusive anomaly detection system for comprehensively monitoring communication within ICS.
About Product
Description
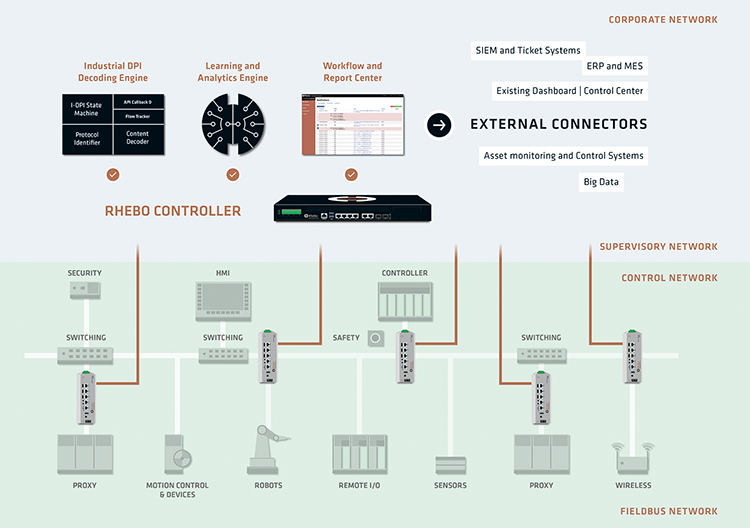
Rhebo Industrial Protector monitors and ensures the continuous, correct, and predictable operation of real-time Industrial Control Systems to prevent outages and reduce downtimes. Data traffic in control networks is recorded and analyzed to automatically detect and report any anomalies.
Rhebo Industrial Protector ensure operational continuity in production environments and critical infrastructures and protects from security breaches and cyberattacks from inside or outside. Operators of Industrial Control Systems benefit from Rhebo’s solution by enormous cost savings due to the reduction of system outages.
The solution was developed specifically for environments which work with industrial protocols like EtherCAT, Profinet or IEC-104, and supports specific functions such as deterministic communication models, data integration for continuous improvement and automation as well as prioritization of remediate actions.
Rhebo Industrial Protector continuously analyzes the communication in the ICS and evaluates it for anomalies. Both security-relevant incidents and technical error conditions are reliably recorded, evaluated and reported in real-time - no matter if they were previously known or yet unidentified.
The solution was developed specifically for environments which work with industrial protocols like EtherCAT, Profinet or IEC-104, and supports specific functions such as deterministic communication models, data integration for continuous improvement and automation as well as prioritization of remediate actions.
Rhebo Industrial Protector continuously analyzes the communication in the ICS and evaluates it for anomalies. Both security-relevant incidents and technical error conditions are reliably recorded, evaluated and reported in real-time - no matter if they were previously known or yet unidentified.
Benefits with Rhebo Industrial Protector:
- Continuous visualization of all devices, connections and communication flows in the ICS as well as their respective properties.
- Reporting of all security-related and technical anomalies in real-time, distincted in first-time and recurrent events.
- Immediate risk assessment through risk score and specification of each anomaly as security or network quality incident.
- Detailed forensic analysis and remedy assessment through storage of all incident details including a copy of the raw data as PCAP.
- Easy integration of network visibility into existing backend systems through universal interfaces and automatable transfer rules.
Scheme of work