Problems that solves
Risk or Leaks of confidential information
Risk of data loss or damage
No control over the state of communication channels
Unauthorized access to corporate IT systems and data
Values
Ensure Security and Business Continuity
Manage Risks
Skybox Change Manager (CM)
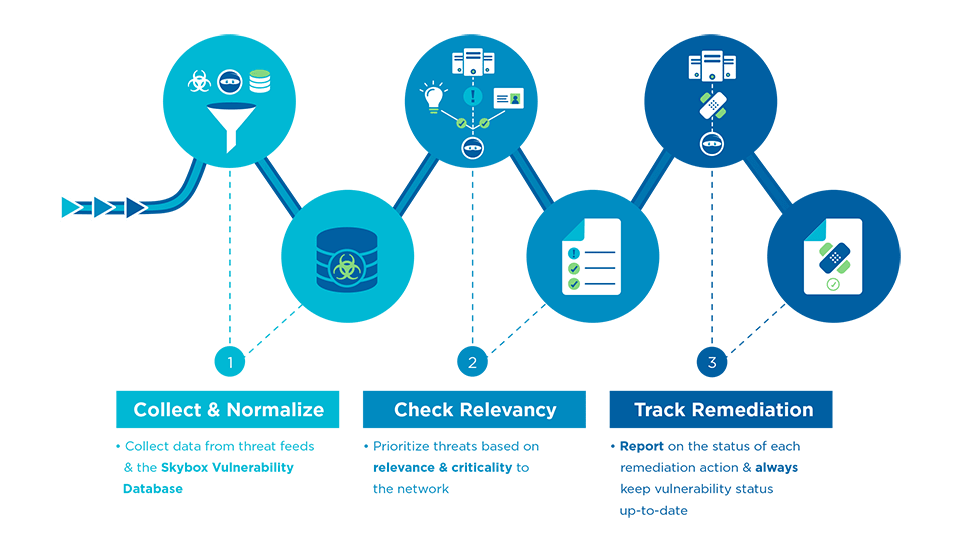
Skybox Change Manager ends risky changes with its automated modeling capabilities and closed-loop rule life cycle management.
About Product
Description
Enterprises have to deal with a constant stream of firewall change requests. Despire the pressure that may be felt by the volume of those requests, or any implementation errors, it’s important that availability, security and compliance are not compromised. Skybox® Change Manager fully automates firewall change management workflows, including rule creation, recertification and deprovisioning. And its analytics–driven automation ensures each change is properly handled from request to implementation and verification.
Change Manager delivers automated modeling capabilities to assess potential business impacts, and closed-loop rule life cycle management to verify that every change is executed as intended. With customized, automated workflows, IT security teams can improve change management efficiency by up to 80 percent.*
With Skybox Change Manager, you can:
- Fully automate firewall change management workflows, improving communication and efficiency across security teams
- Validate proposed firewall changes by checking for access and rule policy violations, as well as new vulnerabilities
- Use formalized tickets and closed-loop workflows to ensure changes match the original intent
- Customize and simplify processes to reduce change management time by 80 percent*
- Establish end-to-end rule life cycle management for secure infrastructure and optimized firewalls
- Reduces the chance of human errors and rollbacks of incorrect changes
- Enables customizable change workflow based on type of request
- Ensures accurate change planning and implementation within the context of the network
- Provides option for automated provisioning for select firewall changes
- Automates rule recertification workflow
- Calculates change risk to inform decisions on when next to review rule
- Streamlines review process by maintaining information on stakeholders
- Identifies potential compliance issues and vulnerability exposures to new portions of the network a proposed change could introduce
- Models change impact on network security and compliance before implementation
- Establishes a fully automated approval process from change request through implementation and verification
- Delivers a complete and verifiable audit trail and change reconciliation report
- Provides closed-loop change management capabilities to ensure all changes are implemented as intended
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief Technical Officer
Chief IT Security Officer
Organizational Features
GDPR Compliance
Internet access is available for employees