Categories
Problems that solves
No IT security guidelines
Risk or Leaks of confidential information
No monitoring of corporate IT processes
Non-existent or decentralized IT incidents' management
Risk of attacks by hackers
Risk of data loss or damage
Insufficient risk management
Values
Ensure Security and Business Continuity
Ensure Compliance
Manage Risks
The Chertoff Group Cyber Security Risk Management
Solution helps clients to build effective cyber and physical security programs by assessing, managing and monitoring enterprise threats.
About Product
Description
Cyber effectiveness
The last decade has seen major increases in cyber regulation and investment, and yet cyber risk has only grown. 2017 occasioned some of the most costly and disruptive cyber attacks in history. Executives across sectors are asking, how do we know if we have an effective cyber security program?
Countermeasure Assessment: Focus on most risk-reducing controls. As an option, weighted score range based on level of implementation and perceived risk reduction
Testing & Validation: Analyze results from external risk scoring vendor as an option
- Apply an offense-informed defense analysis to assess technology environments from the mindset of an adversary
- Approach prioritizes preventive measures based on risk.
- Design-in the changing nature of inherent risk into program oversight, and our methodology also accounts for implementation risks so organizations avoid trip-ups as they build their programs
- Ensure programs address inherited risk from third-party dependencies
- Stress the importance of testing and continuous monitoring of mitigation measures to demonstrate security performance
Who The Chertoff Group do it for
- Organizations needing a comprehensive evaluation of a security program with technical validation
- Executives who need quick-turn program evaluation or critical third party review
- Organizations needing a comprehensive program build, designed for effectiveness
How they do it
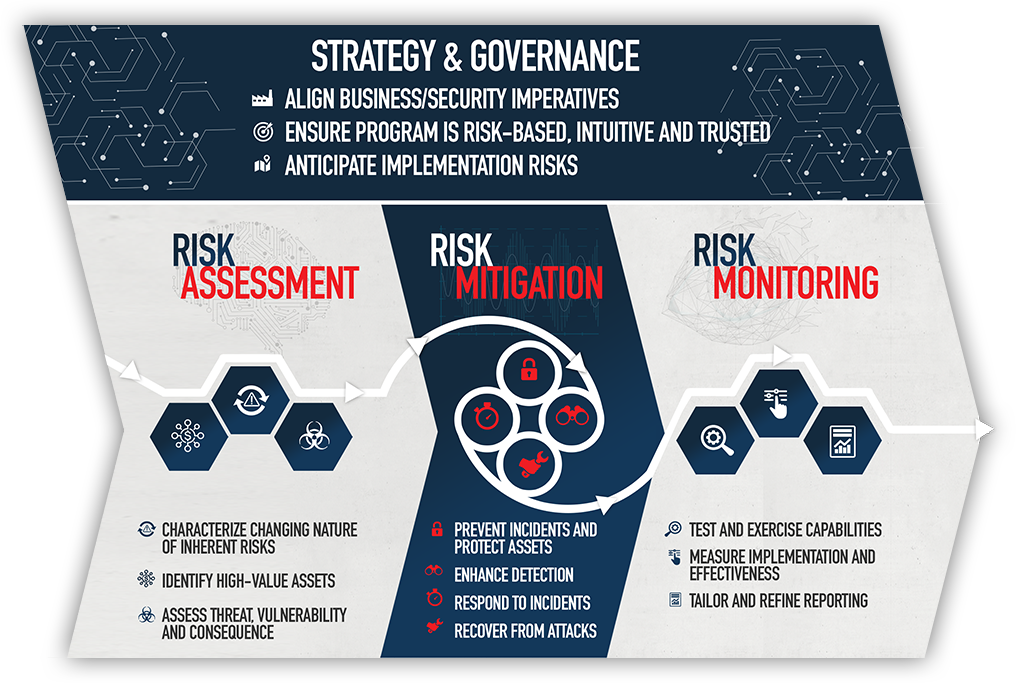
Approach is grounded in the belief that effective security is not an end-state so much as it is a continuing process – founded in a cycle of activity to assess, mitigate and monitor security risk. Team works continuously to incorporate insights they learn from client projects, discussions with government stakeholders and interactions with solution providers into the security risk management framework.Risk Assessment
Compliance mandates are a “necessary but not sufficient” – planning must reflect changing business, technology, customer, regulatory and threat drivers. Countermeasures must be aligned to reasonably foreseeable threat tactics, techniques and procedures.Risk Mitigation
Constrain rapid spread and enable security operations to quickly and authoritatively identify, contain and recover from a compromise. Anticipate implementation risks.Risk Monitoring
Build in meaningful opportunities to measure program advancement through multiple lenses (risk-based countermeasures, operational performance, testing, etc.).Solutions
Cyber Risk Management Program Build Governance Assessment: DEEP-DIVE RISK ASSESSMENT plus…- Security strategy document
- Review of policies / standards library
- Implementation planning guidance
- Security Planning, Implementation & Reporting, informed by lessons-learned from testing, managed services, incident response and exercises
- Security Tool Optimization
- Managed Services as an option
- Incident Response Services as an option
- Exercises
- Program metrics
- Ongoing measurement & interpretation
- Evaluation of inherent risk factors
- Consideration of key implementation risks
- Full controls assessment mapped to authoritative framework
- TTP/threat pathway analysis based on MITRE ATT&CK model
- Insights from technical testing
- Vulnerability assessment
- Internal and external pen testing
- Tool optimization analysis
Countermeasure Assessment: Focus on most risk-reducing controls. As an option, weighted score range based on level of implementation and perceived risk reduction
Testing & Validation: Analyze results from external risk scoring vendor as an option
Scheme of work