
Problems that solves
Risk or Leaks of confidential information
Malware infection via Internet, email, storage devices
No monitoring of corporate IT processes
Risk of data loss or damage
Risk of attacks by hackers
Values
Ensure Security and Business Continuity
Support Decision Making
Manage Risks
About Product
Description
Verint powers national and organizational security operations centers (SOCs) with an intelligence-driven, data mining cyber security platform to secure nations, government, critical infrastructure, and enterprise organizations.
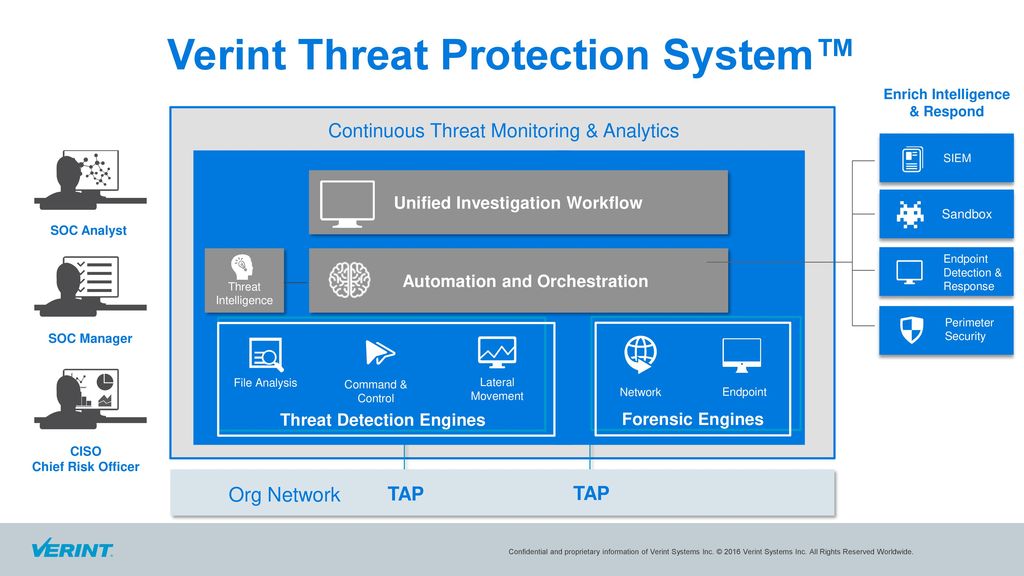
Verint Threat Protection System deployed within the SOC features multiple advanced detection engines monitoring the network, endpoints and payloads, proactive forensics gathering and advanced investigation tools. Alerts are automatically investigated, reducing labor-intensive manual processes and providing SOC analysts with visual, prioritized incident storylines and remediation tools through a single pane of glass.
Early Detection of Complex Threats
Early detection of unknown threats via multiple detection sensors, leveraging machine learning, data mining and behavioral analysis.
100% Alerts inspection
Automated cyber investigations cover 100% alerts - validating every threat and eliminating time otherwise spent on false positives.
Simplified Cyber Investigations
A single unified investigation platform replaces multiple security tools - simplifying security operations, accelerating analysts' ramp-up and lowering the skill barriers. The principles of Verint Threat Protection System HOLISTIC KILL-CHAIN COVERAGE
100% ALERTS INSPECTION WITH VIRTUAL ANALYSTS WORKING 24/7
IMPLIFY CYBER INVESTIGATIONS THROUGH A SINGLE PANE OF GLASS
Early detection of unknown threats via multiple detection sensors, leveraging machine learning, data mining and behavioral analysis.
100% Alerts inspection
Automated cyber investigations cover 100% alerts - validating every threat and eliminating time otherwise spent on false positives.
Simplified Cyber Investigations
A single unified investigation platform replaces multiple security tools - simplifying security operations, accelerating analysts' ramp-up and lowering the skill barriers. The principles of Verint Threat Protection System HOLISTIC KILL-CHAIN COVERAGE
- Multiple sensors continuously monitoring and gathering forensics from the network, endpoints and files.
- Full Endpoint Detection and Response (EDR) - endpoints are monitored continuously by inspecting files, processes, communications, registry, devices and more.
- Behavioral analytics go beyond signatures to identify C&C communications and lateral movements within the network.
100% ALERTS INSPECTION WITH VIRTUAL ANALYSTS WORKING 24/7
- Thousands of alerts are automatically investigated and cross referenced with current and past security events.
- Valid alerts are fused into prioritized security incidents, along with all findings and forensic evidence.
- Incident findings are fully documented for further investigation and collaboration.
IMPLIFY CYBER INVESTIGATIONS THROUGH A SINGLE PANE OF GLASS
- Unified investigation platform - multi-dimensional detection, forensics, automated investigation and orchestrated response.
- Visual attack and investigation storylines, graphical link analysis, one-click forensics and evidence gathering.
- Orchestrated response via open APIs to perimeter security tools.
Scheme of work
Competitive products
Deployments with this product
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief Technical Officer
Chief Technical Officer
Chief IT Security Officer
Organizational Features
Сonfidential data
Internet access is available for employees
GDPR Compliance




















