Categories
Problems that solves
Malware infection via Internet, email, storage devices
Non-existent or decentralized IT incidents' management
IT infrastructure downtimes
Risk of attacks by hackers
Insufficient risk management
Values
Ensure Security and Business Continuity
Manage Risks
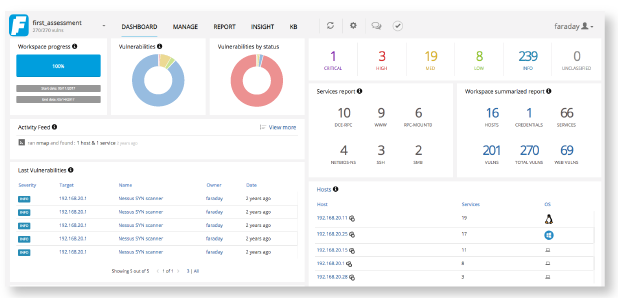
Faraday Platform
Integrated Penetration-Test Environment, a multiuser Penetration test IDE. Designed for distributing, indexing, and analyzing the data generated during a security audit.
About Product
Description
Faraday was made to let you take advantage of the available tools in the community in a truly multiuser way.
Designed for simplicity, users should notice no difference between their own terminal application and the one included in Faraday. Developed with a specialized set of functionalities, users improve their own work. Do you remember the last time you programmed without an IDE? What IDEs are to programming, Faraday is to pentesting.
Plugins
You feed data to Faraday from your favorite tools through Plugins. Right now there are more than 70+ supported tools. There are three Plugin types: console plugins which intercept and interpret the output of the tools you execute, report plugins which allows you to import previously generated XMLs, and online plugins which access Faraday's API or allow Faraday to connect to external APIs and databases. Supporting output from +70 tools, Faraday Platform centralizes all your efforts and gives sense to your main objectives. Providing powerful Automation Technology, it helps you reduce your findings’ life cycle by prioritizing actions and decreasing the exposure time of your assets, promoting collaboration by allowing big and small groups of people to work together. Plus, get deep insight on all your projects with just a couple clicks.Key features
Custom Implementation. No infrastructure changes needed: implement Faraday On-prem, Cloud or Hybrid without network changes. Flexible Integrations. Import output or results from 3rd party tools and synchronize your ticketing systems (JIRA, ServiceNow) and security enhancements (2FA, LDAP) Workflows. Implement custom events by triggering actions or vulns' content in real time Deduplicate Vulns. Faraday's Global Vuln KB allows you to customize descriptions and apply them accordingly. Agents. Define and execute your own actions from different sources and automatically import outputs into your repository. Scheduler. Automate repetitive Agents' actions and check results on your Dashboard. Graphics. Get a visual representation of all your findings with just one click. Faraday Client. Solution’s shell allows you to upload results while pentesting actively. Methodology and Tasks. Setup your own strategy, assign tasks to users for each phase and easily follow them up.Choose the plan that best: fits your needs
Community Faraday supports the InfoSec Community around the globe by offering a free open source version that improves on daily workflows- Feed data to Faraday from your favorite tools
- Divide projects by your own rules
- Customize your instance
- Easily identify and sort your database
Craft and export projects using your own templates
Plan ahead and keep track of your goals
- Prioritize actions, decreasing exposure time for your assets
- Adapt strategies to customize every phase of your projects
- Integrate everything!
Scheme of work