Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
Shortage of inhouse IT engineers
High costs of IT personnel
Values
Reduce Costs
Enhance Staff Productivity
About Product
Description
Attribute based access control (ABAC) is an information technology and architecture for automated, externalized digital authorization, as described by NIST. ABAC includes a policy decision service that evaluates digital policies against available data (attributes) and renders a decision to permit or deny access to the requested resource.
ABAC (Attribute Based Access Control)
Attribute Based Access Control (ABAC) decouples authentication and authorization, separating "who you are" from "what you can do." ABAC evaluates available descriptive data (attributes) against stored policies to determine whether the user is authorized to access the requested resource. In ABAC, user roles become another data attribute among many attributes that can be consumed, or referenced against prevailing security policies, by the system for an authorization decision. Jericho Systems’ EnterSpace Decisioning Service™ is a sophisticated content filtering software technology that supports ABAC’s decision-making and authorization capabilities. Jericho subject matter experts have contributed to NIST Special Publication 800-162, Guide to Attribute Based Access Control (ABAC) Definition and Considerations.
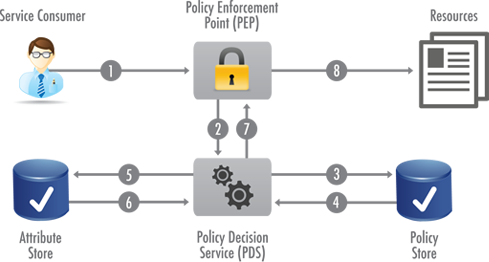
The basic components of attribute based access control (ABAC) are:
- Policy Store. The policy store is a collection of logical rules and policies that guide access decisions.
- Policy Editor. The policy editor is a software tool that allows administrators to create and edit policies that are evaluated and enforced by the decision engine.
- Policy Information Point. The policy information point (PIP) encompasses enterprise data stores such as LDAP, MySQL, or Oracle that hold relevant details, or "attributes." Attributes are the data points used to evaluate a user's request against policy.
- Policy Decision Service. The policy decision service is an "engine" that evaluates user requests against relevant policies and attributes, renders a decision about access, and triggers appropriate system responses and actions.
- Policy Enforcement Point. The policy enforcement point (PEP) intercepts requests for access, and forwards them to the policy decision service for authorization.
Scheme of work