Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
Shortage of inhouse IT engineers
High costs of IT personnel
Values
Reduce Costs
Ensure Security and Business Continuity
SecZetta Third-Party Identity Risk
SecZetta’s Third-Party Identity Risk solution provides a comprehensive set of capabilities that help organizations improve the operational efficiency
About Product
Description
The Problem
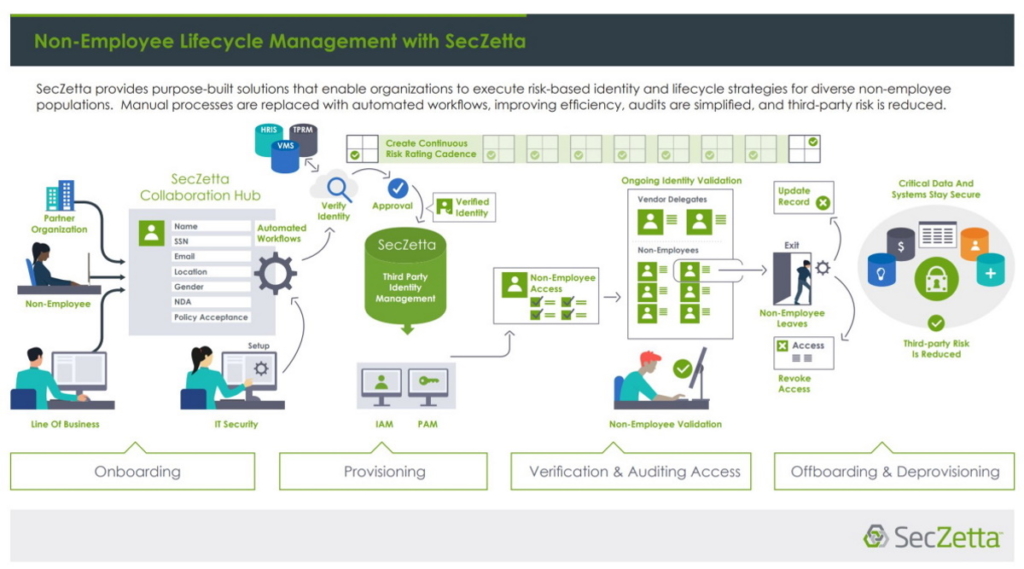
Organizations in almost every industry are relying on growing and increasingly diverse numbers of third parties (contractors, vendors, partners, affiliates, volunteers, students, and freelancers) to quickly and cost-effectively meet operational needs. Interestingly, these resources are not limited to humans, and may also include a bots, service accounts, and IoT (Internet of Things) devices.
Unfortunately, most organizations have no way to centrally track and manage the relationships with their non-employees and therefore struggle with granting appropriate access to enterprise assets. SecZetta enables organizations to execute risk-based identity access and lifecycle strategies for vendors, partners, contractors, freelancers, bots, service accounts, and other non-employee populations.
Our Solution
SecZetta’s Third-Party Identity Risk solution provides a comprehensive set of capabilities that help organizations improve the operational efficiency and reduce the cost and risk of managing third party identities. Because third parties are widely acknowledged by security professionals as high risk, special consideration is taken at the individual identity level when providing them with insider access to facilities, systems, and data. With SecZetta, organizations have better transparency into the dynamic relationships they have with each individual third-party identity and are thus able to make well-informed, risk-based decisions about provisioning, verifying, and deprovisioning access.
The SecZetta Third Party Identity Risk solution is purpose-built to uniquely manage the dynamic relationships organizations have with non-employees in a single, easy-to-use application that helps IT teams:
- Facilitate commercial initiatives by improving IAM business processes
- Support regulatory compliance and other audits
- Reduce third-party risk
- Identity Lifecycle
- Identity Risk
- Identity Collaboration
Scheme of work