Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
Shortage of inhouse IT engineers
High costs of IT personnel
Values
Reduce Costs
Ensure Security and Business Continuity
ShieldIOT Network Security
Fast and accurate anomaly detection, with no expertise required
About Product
Description
The ShieldIOT AI-based network anomaly detection solution analyzes device communications to identify the first signs of cyber-attacks and operational anomalies. Deployed at the IoT network operator / service provider cloud, the agent-less solution is highly scalable, protecting massive multi-application IoT networks against various threats including DDoS, unknown malware, ransomware, communication hijacking, node takeover and replication, replay attacks, data falsification and many more.
Features:
- Unmatched Accuracy. ShieldIOT Corset-based AI anomaly detection is x5 to x20 more accurate compared to leading industry solutions
- Real-Time Detection. From one week to one minute. No speed or accuracy trade-offs. Detect the first signs of attack before damage takes place.
- Actionable Alerts. Attack type, duration, affected devices, score, severity, trigger features… Enabling automated or non-expert threat mitigation
- Unlimited Scalabilty. Transforms huge volumes of big data into small data sets. Agent-less solution with no device or network changes
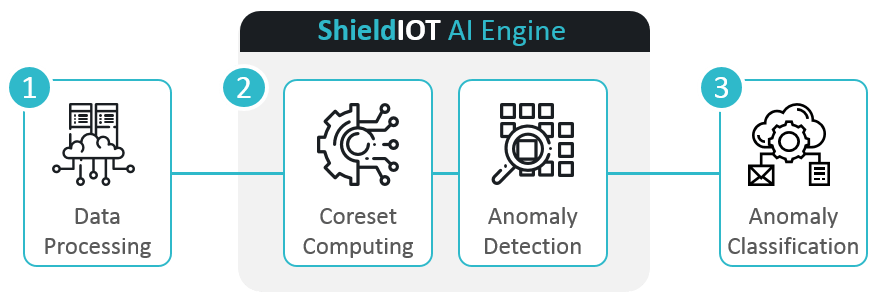
- Data Processing. Data filtering, null completion, data sources joining, data enrichment, feature engineering
- AI Engine. Coreset computing to reduce the data, followed by running a set of AI and machine learning detection models.
- Anomaly Classification. Automatically generate event type, by combining patented labeling process with domain expertise
Scheme of work