Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Reduce Costs
Enhance Staff Productivity
Honeywell ICS Shield
Cyber security management platform for securing connected industrial control system (ICS) environments
About Product
Description
What Is It?
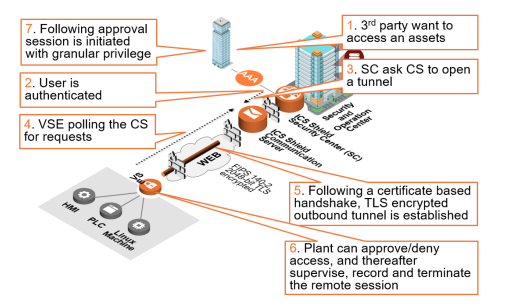
ICS Shield is Honeywell’s top-down OT security management platform for securing connected Industrial Control Systems (ICS)/SCADA environments. Empowering organizations to implement connected operations while minimizing security vulnerabilities, ICS Shield secures remote field assets from a single security and operations center. This field-proven technology automates the deployment and enforcement of plant-wide security policies while focusing on security essentials.How Does It Work?
Discover. The first step in protecting an OT environment is identifying precisely what’s on the network. ICS Shield helps you achieve an accurate inventory of your ICS assets including hardware, software and service configurations. Connect. To maintain high levels of security, uptime and safety of distributed devices, secure remote access to field assets is required by first- and third-party personnel and machines. Providing extremely granular and robust AAA remote access, ICS Shield ensures secure remote access and monitoring, protected file distribution to devices, and safe data transfer from plants to HQ for analysis and risk management. Protect. ICS Shield unifies and automates the policy management process, empowering the creation, deployment and enforcement of plant-wide and granular security policies. Leveraging ICS Shield’s security policy management, operations and control teams significantly improve OT security and compliance. Scale. ICS Shield infrastructure is designed for multi-site, multi-vendor deployment, with all sites connected to the security and operations center via Honeywell’s Secure Tunnel. This distributed architecture guarantees data security and integrity. Features: Secure remote access Allows remote users to connect to devices in the site via RDP and VNC protocols. Site administrators can set security policies to govern remote access (can allow/deny/require manual approval for all connections, or set policy for individual users). Encrypted two-factor authentication Provides an additional layer of security for all users connecting to a Security Center. In addition to requiring a username and password, users must provide further proof of their identity. This is often something like an RSA token that generates a second numeric password which changes several times every minute. When logging in, users must provide their username and password along with this secondary password. Password vault Allows administrators of a site to store remote access passwords in a local "vault". Approved remote access users can connect with these credentials without the site administrator needing to share the passwords. This eliminates the need to share plaintext passwords with users, and simplifies changing system passwords to meet security policies (remote users don't need to worry about the password changes) Complete auditing Creates a complete recording of all remote access sessions which can be played back at any time from the Security Center. Details about authorized remote access sessions can also be included in reports. Initial active asset discovery An administrator provides appropriate credentials to the active asset discovery, which then searches the network for PC and network devices, and tries to gather information about them using those credentials. As part of the Essential bundle, this is a one-time discovery to populate the device database initially, but not find devices that are added/removed/changed in the future.Scheme of work