
Categories
Problems that solves
Risk or Leaks of confidential information
Unauthorized access to corporate IT systems and data
Risk of attacks by hackers
High costs
Values
Reduce Costs
Ensure Security and Business Continuity
Intrinsic ID QuiddiKey
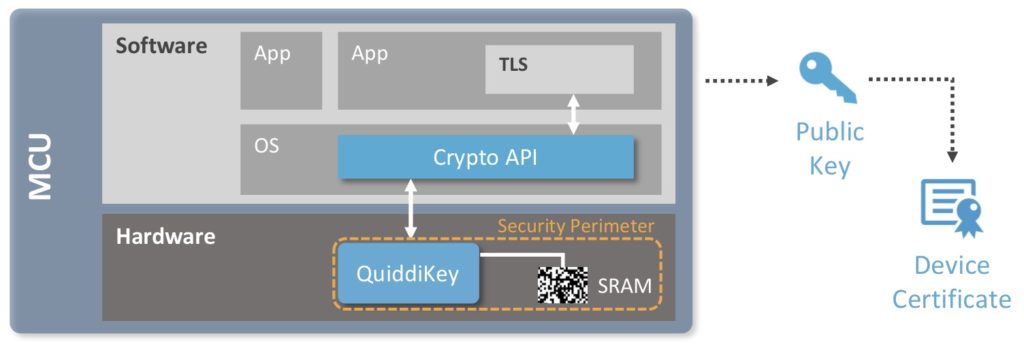
QuiddiKey is an embedded hardware IP that creates the secret key of the unclonable identity from within, derived using the intrinsic randomness in uninitialized SRAM.
About Product
Description
The accelerating expansion of the Internet of Things brings with it a comparably expanding threat model. The growing number of endpoints require strong identities as the foundation of trust to establish and scale robust security. QuiddiKey is a secure root key generation and management solution that allows device manufacturers to secure their products with an internally generated, unique identity without the need for adding costly, security-dedicated silicon. The hardware IP is based on SRAM Physical Unclonable Function (PUF) technology and is the foundation of a device’s hardware-based root of trust. The IP is agnostic to fab and technology choice and has been deployed in 150 million+ devices. QuiddiKey not only improves time to market and delivers better security at lower TCO, but paves the way for scaling the IoT to billions of devices.
Unclonable Identities for the IoT
To solve security problems in IoT systems, such as authentication, product lifecycle management, reverse engineering and cloning, every device needs an unclonable identity. This consists of a secret key, a public key and a certificate. The biggest challenge is to get these credentials into the device. QuiddiKey is an embedded hardware IP that creates the secret key of the unclonable identity from within, derived using the intrinsic randomness in uninitialized SRAM. This secret key is not stored but is dynamically regenerated from the SRAM PUF inside a secure perimeter.
Completing the unclonable identity requires that a public key be generated from the secret key. And this public key can be turned into a certificate by signing it at a certificate authority. At that point, the device is ready to prove its identity and set up a secure channel with another device, a server or a cloud.
Security Based on SRAM PUF
At power-up, SRAM bits settle in the one or zero states in a non-deterministic way that not even the manufacturer can predict or duplicate. That’s what makes it a physical unclonable function, or PUF, which can be used as a unique “silicon fingerprint.”
An SRAM PUF response is a noisy fingerprint, and turning it into a high-quality and secure key vault requires further processing. This is done with the QuiddiKey hardware IP. QuiddiKey reliably reconstructs the same cryptographic key under all environmental circumstances. Upon first use, called the enrollment, it generates an activation code (AC) which, in combination with the SRAM startup behavior, is used to reconstruct on-demand, in real-time, an intrinsic PUF key. This PUF key is never stored in flash or OTP. When it is needed later it can be reconstructed.
The intrinsic PUF key can be used as a root key for key derivation and key wrapping. A key protected by QuiddiKey is integrity protected and can be retrieved only on the same device while it will be meaningless on other devices.
QuiddiKey is available in two configurations:
- QuiddiKey-Plus. Device-unique key creation, derivation, wrapping and management.
- QuiddiKey-Safe. Device-unique key creation and derivation.
- Use standard SRAM
- Unclonable and immutable
- Device-unique high-quality keys
- No secrets when power is off
- No root key programming
- Flexible and scalable
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
IT Security Department in company

















