Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Reduce Costs
Enhance Staff Productivity
ss8 Insider Threat Detection
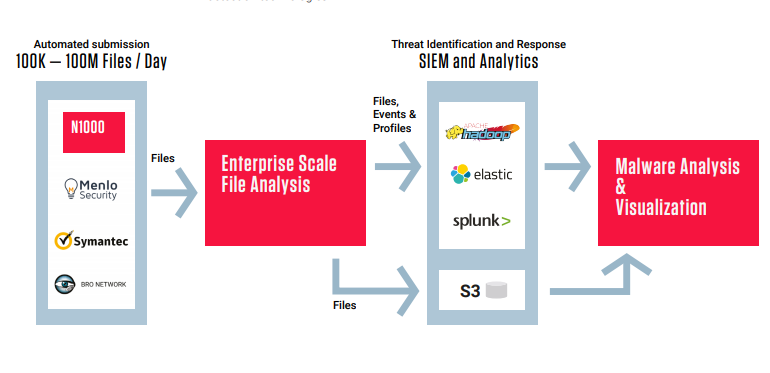
SS8 Insider Threat Detection generates and analyzes high-definition network records from internal communications
About Product
Description
SS8 Insider Threat Detection generates and analyzes high-definition network records from internal communications, providing a proactive solution to identify and retrieve key activities from users across your computer network.
Key Components
The SS8 Insider Threat Detection (ITD) solution provides the proactive alerting and investigation workflow needed to precisely identify suspected insiders and track their pattern of life within the network.
Sensor + PXE
Deployed on the internal network to records East/West traffic
Enrichment
User ID collected and correlated via directory store (Active Directory, DHCP)
Analytics
SS8 DRAP engine stores and scores user/device activity over time
ITD Discovery
SS8 ITD discovery interface alerts on flagged users, and enables querying of file transfer activity
Intellego
SS8 Intellego can examine full packet and perform reconstruction
Additional Features and Benefits
Enrich Activities
SS8 can enrich a recorded history of network behaviors with user, device, and location information, helping you answer more specifics about an insider threat.
Apply Analytics
SS8 applies recursive analytics to a suspected insider’s pattern of life on the network, enabling you to spot behaviors that would indicate malicious intent.
Stop Malicious Intent
Protect your IP by detecting large file transfers, repeated small file transfers, and device connections with unauthorized servers or personal cloud-storage.