Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Enhance Staff Productivity
Reduce Costs
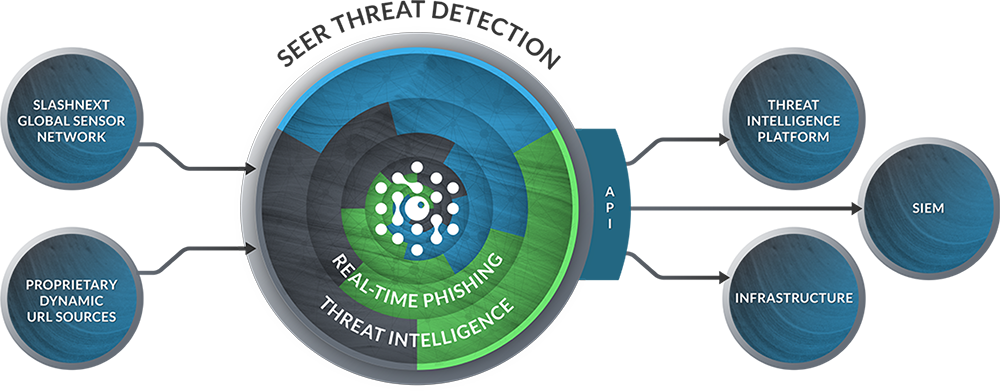
SlashNext Real-Time Phishing Threat Intelligence
The Industry’s Broadest, Most Up-to-the-Minute Intelligence on Phishing Threats
About Product
Description
With SlashNext Real-Time Phishing Threat Intelligence, security teams can better understand and protect their organizations from sophisticated, zero-hour phishing attacks. With tens of thousands of new phishing site detections per day, plus automated URL re-checking and retirement, SlashNext provides the broadest real-time phishing threat intelligence available.
- Credential Stealing
- Scareware
- Rogue Software
- Phishing Exploits
- Social Engineering Scams
- Phishing Callbacks (C2s)
Scheme of work