Categories
Problems that solves
Shortage of inhouse IT resources
Shortage of inhouse software developers
Shortage of inhouse IT engineers
High costs of IT personnel
Values
Reduce Costs
Enhance Staff Productivity
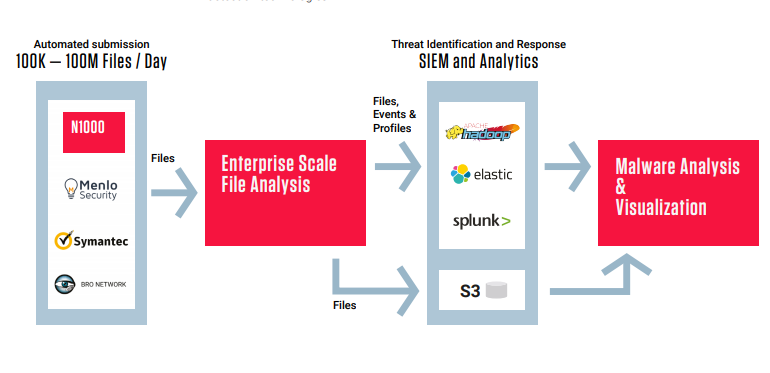
About Product
Description
Data Loss Prevention (DLP) is a strategy for ensuring your employees and vendors do not accidentally or intentionally share sensitive and company confidential data outside your organization. A DLP solution utilizes content discovery, digital inspection techniques and contextual analysis to identify and categorize sensitive data and IP. Next, policies and rules are created for data usage scenarios. The system then monitors user actions; validates them against the DLP rules and takes appropriate action if and when a rule condition is triggered. Actions could include stopping the action, blocking the user, alerting an administrator, requesting management override and more.
Teramind Features:
User activity monitoring:
Monitors all user activity including third-party vendors and privileged users for 12+ system objects like: website, application, keystroke, IM, email, network etc.
Powerful policy and rules engine:
Teramind comes with hundreds of pre-built rules, templates and data categories. Create your own rules with an intuitive, visual Policy & Rules editor.
Insider threat detection:
Intelligent user behavioral analysis combined with session recording & playback, real-time alerts, immutable logs etc. help identify insider threats before they become critical issues.
Content discovery and classification:
Discover and identify sensitive information from structured and unstructured sources. Built-in classification templates for Personally Identifiable Information (PII), Personal Health Information (PHI), Personal Financial Information (PFI) etc.
Advanced OCR:
‘On the fly’ content discovery with advanced OCR, natural language processing (NLP) and RegEx. Detect sensitive data inside images, applications and even videos preventing steganographic data exfiltration.
Clipboard monitoring:
Teramind’s Clipboard Monitoring and Interception feature allows you to protect sensitive data from being shared through the clipboard copy/paste operations.
Fingerprinting and tagging:
Teramind’s powerful fingerprinting and tagging features identify important documents and files and then monitors their usage so that you can keep track of your data even when modified or transferred.
Compliance management:
Teramind has built-in support for compliance and standards like GDPR, HIPAA, PCI DSS, ISO 27001 etc. and can be adapted to support other regulatory requirements with its powerful Policy & Rules editor and various monitoring and reporting capabilities.
Risk management:
Identify high risk users, policies and system objects on the dedicated Risk Dashboard. Sophisticated risk scoring helps identify and focus on high risk areas.
Flexible Deployment Options
On-premise - control the Teramind implementation in its entirety, stay off-cloud if that’s your firm’s operational model, leverage LDAP groups and users to identify which users and groups to apply which policies and rules to.
Teramind Private Cloud - use your own secure, scalable private cloud implementation including AWS, Google Cloud, Azure and more.
Teramind Cloud - trust us the management of the Teramind deployment and infrastructure. Only install Teramind Agents on the machines you want to monitor and set up your users, policies and rules and let us take care of the rest.