Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Enhance Staff Productivity
Reduce Costs
ECI Telecom Muse MCSS
ECI is a global provider of ELASTIC Network solutions to CSPs, critical infrastructures as well as data center operators
About Product
Description
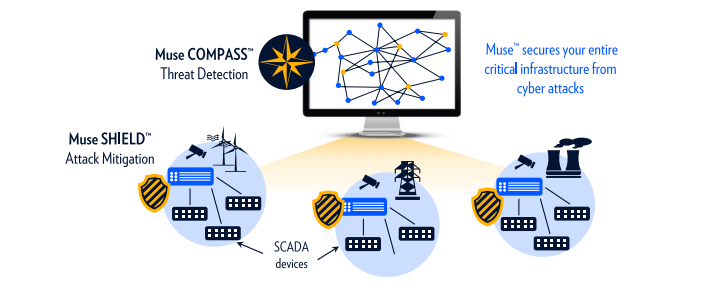
Critical infrastructures (CI) are a prime target for cyber-attacks. National security administrations say that attacks like the Ukraine power grid strike should be a “wake-up call” for CI organizations. Proper protection is a particularly complex matter. It must defend both information and operational technologies (IT/OT), and also must be able to discern tangible threats from a multitude of reported events. ECI’s Muse cyber security suite meets these challenges and more.
Why ECI?
- Prevents Attacks
- Detects Real Threats
- Guards The Security
- Cost Effective
- Best-of-breed SCADA protection and anomaly detection against zero-days attacks and site infiltration
- A secure gateway that includes a next gen firewall and applications control to segregate OT networks and prevent attacks propagation
- L2/L3 encryption against man-in-the-middle attacks
Scheme of work