Problems that solves
Risk or Leaks of confidential information
Unauthorized access to corporate IT systems and data
Risk of data loss or damage
Risk of attacks by hackers
Values
Reduce Costs
Ensure Security and Business Continuity
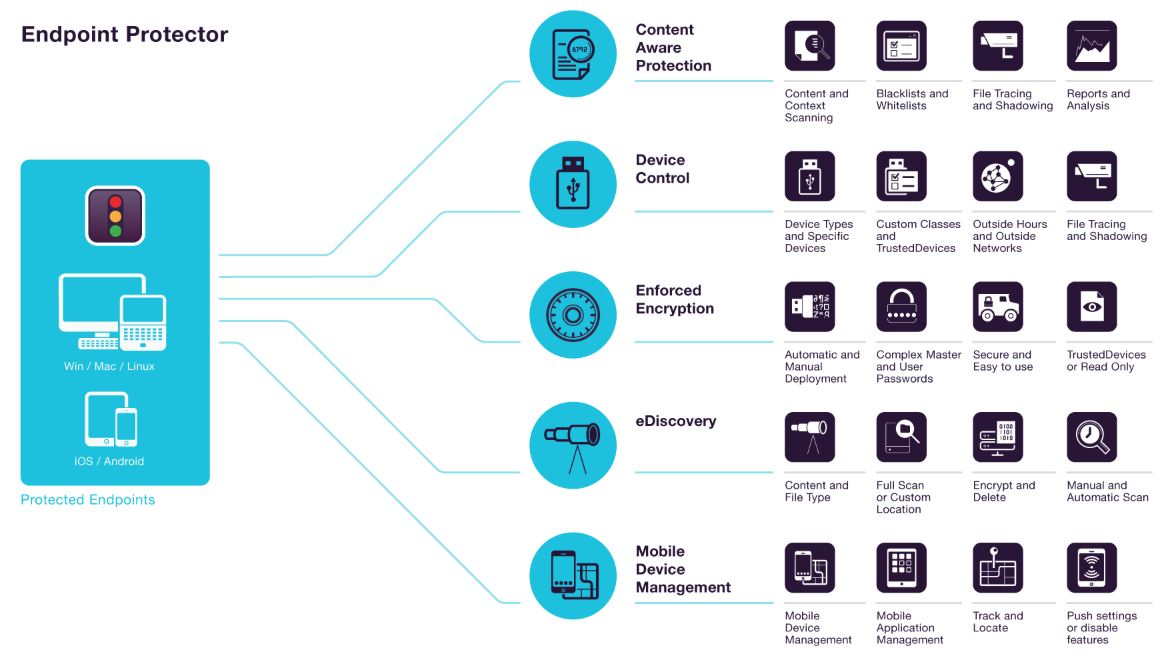
CoSoSys Endpoint Protector
On-premise full DLP for Enterprise and Small-Medium businesses, available as hardware and virtual appliance, or as cloud infrastructure.
Description
Easy to use, cross-platform Data Loss Prevention tools that ensure seamless control of USB and peripheral ports, scan data in motion and data at rest, enforce encryption and offer enterprise mobility management.
Content Aware Protection
Scanning data in motion
Monitor, control and block file transfers. Detailed control through both content and context inspection.
Device Control
USB & peripheral port control
Lockdown, monitor and manage devices. Granular control based on Vendor ID, Product ID, Serial Number and more.
Enforced Encryption
Automatic USB encryption
Encrypt, manage and secure USB storage devices by safeguarding data in transit. Password-based, easy to use and very efficient.
eDiscovery
Scanning data at rest
Discover, encrypt and delete sensitive data. Detailed content and context inspection through manual or automatic scans
Mobile Device Management
Enterprise Mobility Management
Secure, locate and manage mobile devices. Push apps and network settings or remotely wipe data.
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
Internet access is available for employees
GDPR Compliance